-
- Downloads
Merge branch 'master' of...
Merge branch 'master' of gitlab.henriktjader.com:d7018e-special-studies-embedded-systems/are_we_embedded_yet
No related branches found
No related tags found
Showing
- README.md 26 additions, 26 deletionsREADME.md
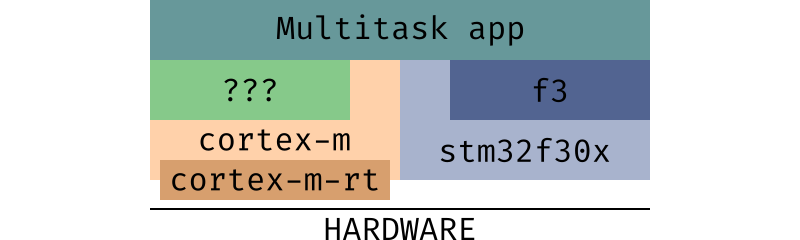
- assets/cortex-m-layers.png 0 additions, 0 deletionsassets/cortex-m-layers.png
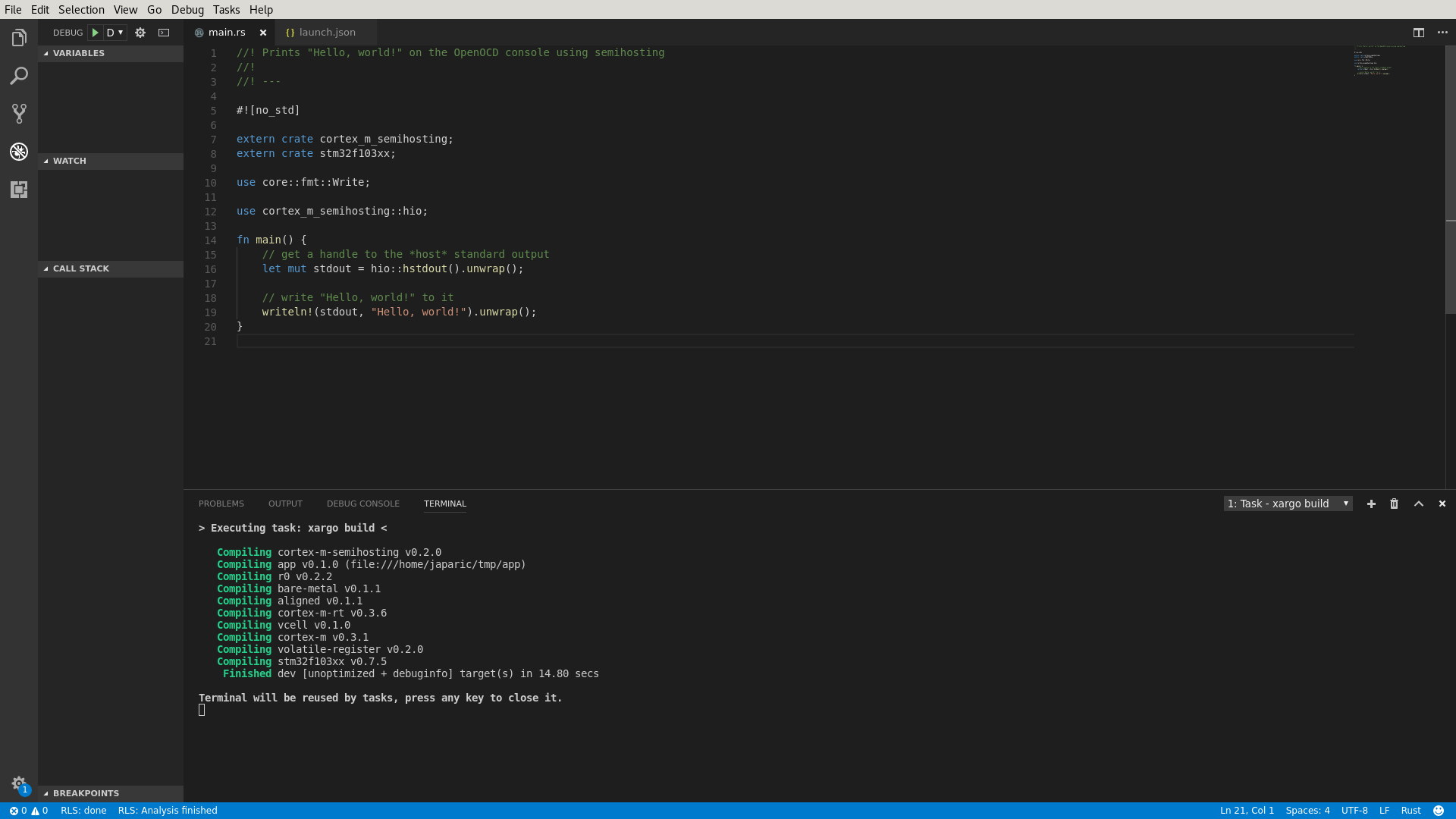
- assets/vscode-build.png 0 additions, 0 deletionsassets/vscode-build.png
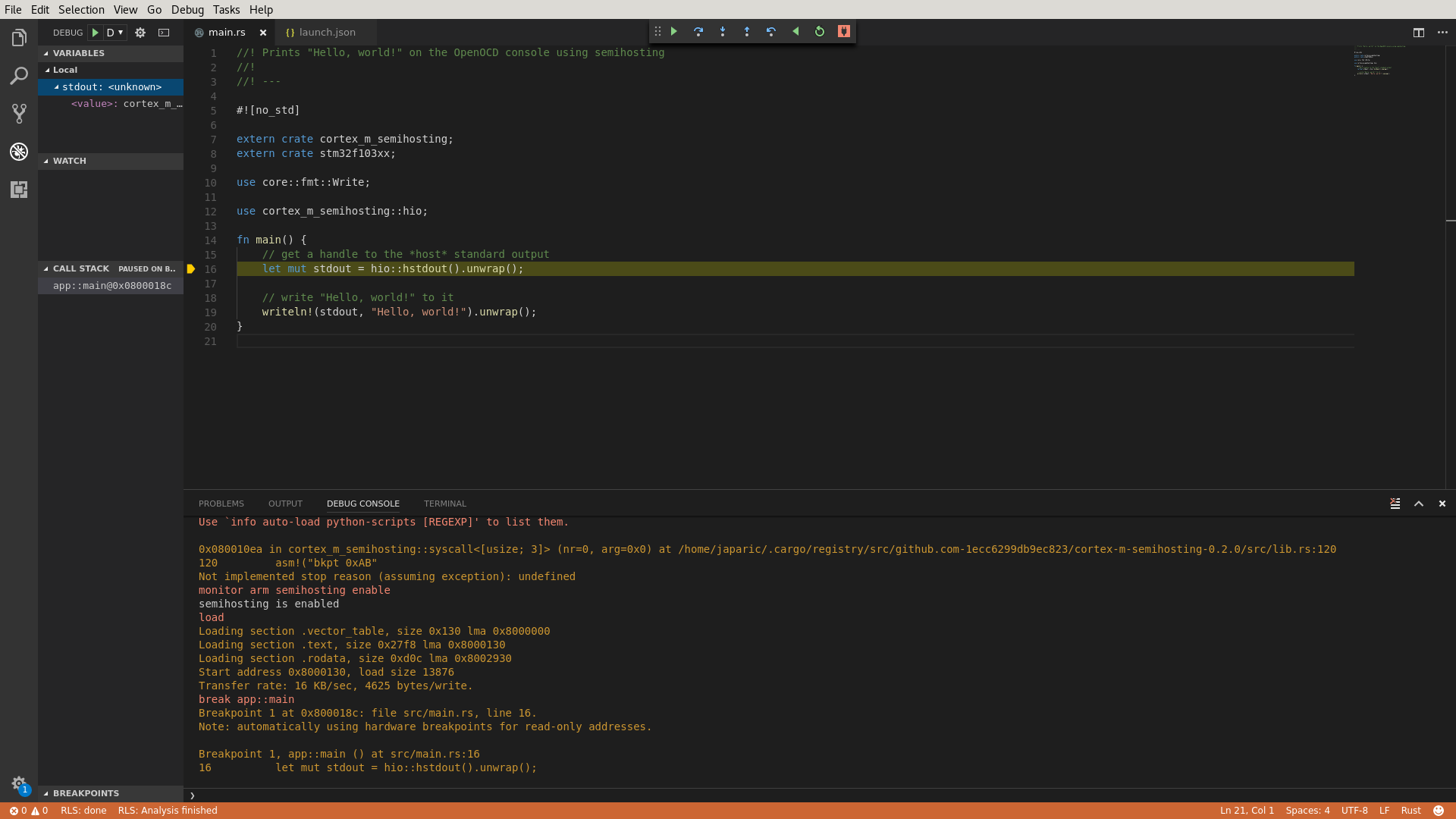
- assets/vscode-debug.png 0 additions, 0 deletionsassets/vscode-debug.png
- doc/Quickstart.md 686 additions, 0 deletionsdoc/Quickstart.md
assets/cortex-m-layers.png
0 → 100644
23.6 KiB
assets/vscode-build.png
0 → 100644
118 KiB
assets/vscode-debug.png
0 → 100644
161 KiB
doc/Quickstart.md
0 → 100644